In the actual production environment, the Authentication of the SharePoint site is not going to be Windows authentication in many scenarios. There are various third party authentication providers are available in the market. Since ADFS is one of Microsoft’s product, It is been widely used by many of the environment. Hence, let us see how to make the Authentication of our web application using ADFS 2.0.
The overall steps are as follows.
1. Installation and Configuration of ADFS 2.0.
2. Create the web application.
3. Adding the SharePoint WebApplication URL as Third Party Relying Party.
4. Export the ADFS Certificate and Copy the same into SharePoint Machine.
5. Create a Trusted Identity Token Issuer.
6. Edit SharePoint WebApplication Authentication.
7. Verify the setup by logging into the Site.
Let us see, each step individually.
1. Installation and configuration of ADFS 2.0.
We had seen about this in the previous article. Refer here to refresh. In our case, the URL of the ADFS Server is https://win2008R2/adfs/ls.
2. Create the Web Application.
This also, we had already discussed here. To make a Claims aware web application, we need to create an https enabled web application. In our case, the URL of the Web Application is https://SathishServer.ss.loc:20003/ and the site collection is /Sites/ClaimsBasedSite.
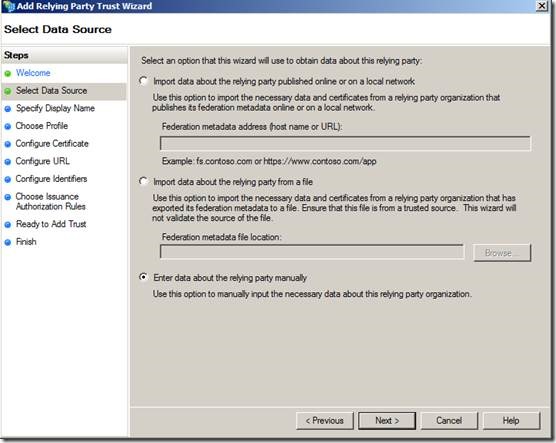
3. Adding the SharePoint WebApplication URL as Third Party Relying Party.
This topic also, covered in a separate article. But that URL is meant for the .Net provider Hosted Application. i.e., we need to make the .Net web application also as a claims aware web application. But in our case, now we are planning to add our SharePoint WebAppliclaiton. Hence the URL should be something like,
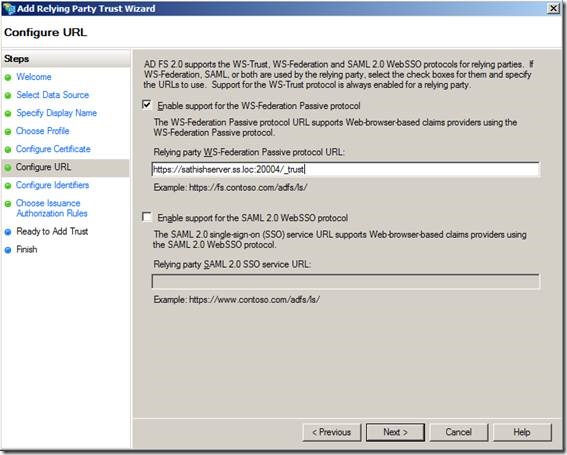
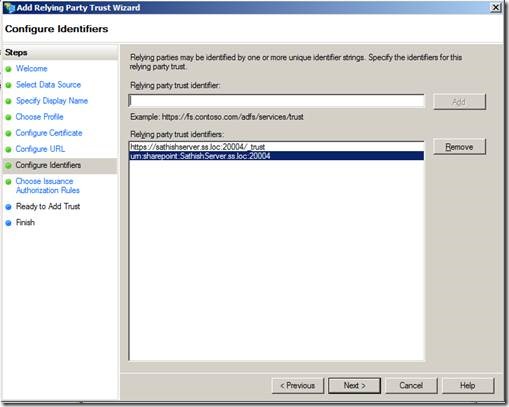
“urn:sharepoint:SathishServer.ss.loc:20003” and https://sathishserver.ss.loc:20003/_trust/.
Let us do a fast recap by the screen shots.
This is where the actual difference comes. You can see the URL which I am giving. It is not the URL of the of the web application. It is appended with “_trust”.
Again here also, we need to add “urn:sharepoint:SathishServer.ss.loc:20003” as the Relying Party trust Identifier”. (Ignore the screen shot as the port is 20004 for different purpose).
The claim rule are similar to that of the previous post. There is no much changes on it.
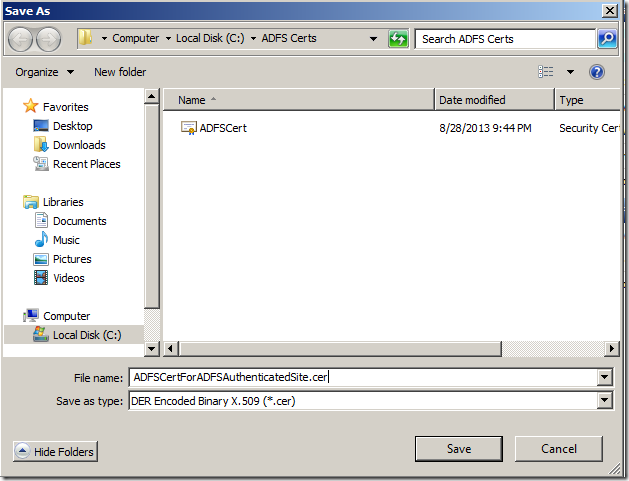
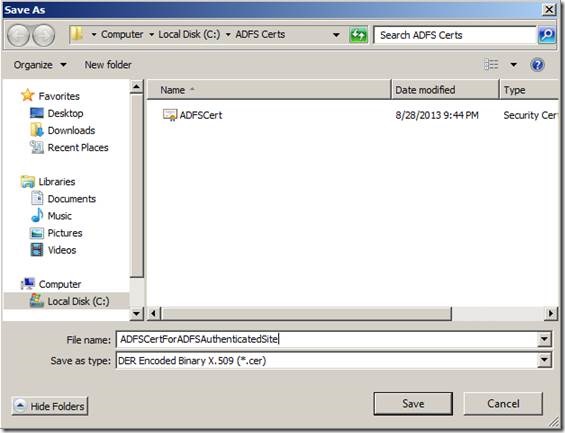
4. Export the ADFS Certificate and Copy the same into SharePoint Machine.
The next step would be exporting the ADFS Token Signing Certificate.
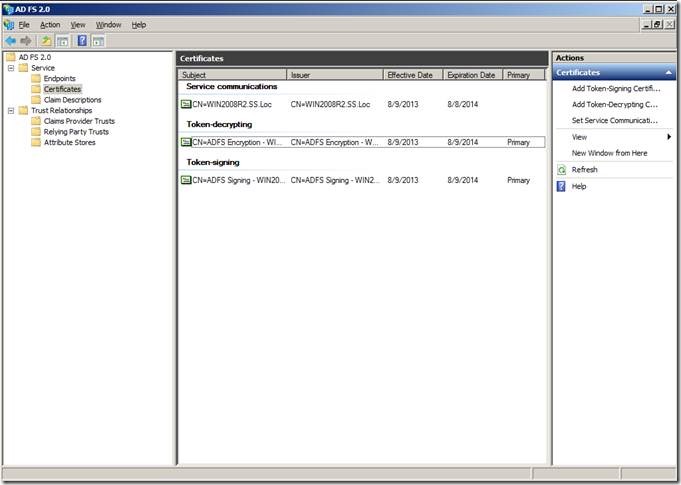
a. Open the ADFS Management Console. And Navigate to the Certificates Node.
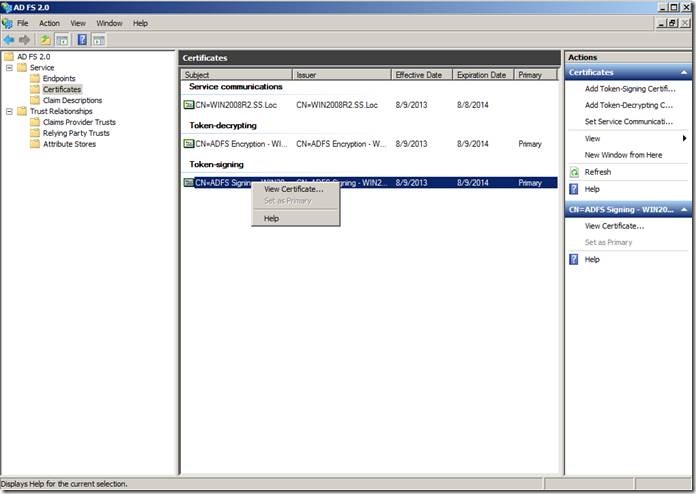
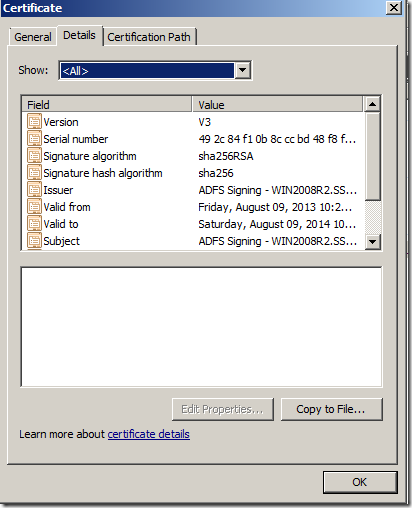
b. Select the Token-signing Certificate and click “View Certificate”
c. On the Details Tab, click “Copy to File…”
d. The wizard will get opened. Follow the wizard as shown in the screen shot.
e. With this, the Certificate has been copied to file with an extension of CER. Copy the file and paste on the SharePoint Server.
5. Create a Trusted Identity Token Issuer.
Now, we need to create a Trusted Identity Token Issuer on the SharePoint Farm. For that, the certificate copied from the ADFS Server is required to be present on the SharePoint Server. Once it is copied, we can execute the below power shell script to create the “Trusted Identity Token Issuer”.
| cls Add-PSSnapin "Microsoft.SharePoint.PowerShell" $Cert = New-Object System.Security.Cryptography.X509Certificates.X509Certificate2("C:\Certs\ADFSCert.cer") New-SPTrustedRootAuthority -Name "Token Signing Cert ADFSAuthenticatedSite" -Certificate $cert $map = New-SPClaimTypeMapping -IncomingClaimType "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress" -IncomingClaimTypeDisplayName "EmailAddress" -SameAsIncoming $upnClaimMap = New-SPClaimTypeMapping -IncomingClaimType "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/upn" -IncomingClaimTypeDisplayName "UPN" -SameAsIncoming $RoleClaimmap = New-SPClaimTypeMapping -IncomingClaimType "http://schemas.microsoft.com/ws/2008/06/identity/claims/role" -IncomingClaimTypeDisplayName "Role" –SameAsIncoming $realm="urn:sharepoint:sathishserver.ss.loc:20003" $signInURL="https://Win2008R2/adfs/ls" $ap1 = New-SPTrustedIdentityTokenIssuer -Name “XYZ” -Description “Test”-realm $realm -ImportTrustCertificate $cert -ClaimsMappings $map,$upnClaimMap,$RoleClaimmap -SignInUrl $signInURL -IdentifierClaim $map.InputClaimType |
· The “Name” attribute describes which authentication provider a Web application is configured for.
· The “Realm” attribute defines the realm to be used by the trusted identity token issuer.
The “ImportTrustCertificate” attribute is what is passed to the token signing certificate copied from the AD FS server in this scenario.
· The “ClaimsMappings” attribute are the claims the trusted identity token issuer will use.
The “SignInUrl” is the URL that users should be redirected to authenticate with the IP-STS. In this scenario, users authenticate with the AD FS server by using Windows integrated security, so they are redirected to the /AD FS/ls subdirectory.
· The “IdentifierClaim” attribute instructs SharePoint Server which of the claims will be the claim used to identify users. In this scenario the e-mail address is used to identify a user.
With this, we successfully created our Trusted Identity Token Issuer. Let us see, how we can change the authentication provider of our SharePoint Web Application.
6. Edit SharePoint WebApplication Authentication.
a. Now, we created our TrustedIdenityTokenIssuer for SharePoint. Let us see, with the web application.
b. Go to the Central Administration.
c. Select the web application for which we need to change the Authentication Providers.
d. Prompted with the popup. Click the default.
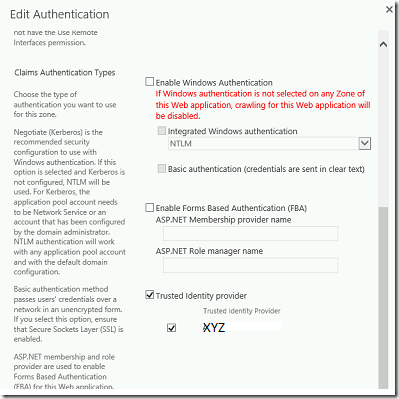
e. Edit Authentication Popup will be shown.
In that, by Default, “Enable Windows Authentication” will be checked. Uncheck it and click “Trusted Identity Provider”. On the below, you can see the list of identity providers, which we created. Click that and Save.
f. That’s it. Now our Web Application is ready to get authenticated by ADFS 2.0.
7. Verify the setup by logging into the Site.
Now we can verify the authentication by login into the site. Type https://sathishserver.ss.loc:20003/Sites/ClaimsBasedSite. After entering the credentials, it will be redirected to https://win2008R2/ADFS/Ls/…… Once, it is authenticated properly, then it will come back to our web application.
8. Trouble shooting.
After following the entire steps, I was facing an issue with the ADFS Authentication. When trying to login to the site, we will be getting some weird exception like “ADFS Exception Occurred” . Normally, SharePoint itself, will not give any clear exceptions. Now again ADFS is also like that only. To see exactly what happens, login to the ADFS Server machine. And go to the EventViewer. On Application Logs, we can see an exception like “The same client browser session has made ‘6’ requests in the last ‘12’ seconds”. By doing some search in the internet, I found a useful link from Steve Psechka. http://blogs.technet.com/b/speschka/archive/2010/08/09/setting-the-login-token-expiration-correctly-for-sharepoint-2010-saml-claims-users.aspx
It was very useful and very clear about the problems. Hence, I am not repeating the points here. Let us get the extract alone. By executing the below script, I get rid of that exception.
| #$sts = Get-SPSecurityTokenServiceConfig #$sts.LogonTokenCacheExpirationWindow = (New-TimeSpan –minutes 1) #$sts.UseSessionCookies = $true #$sts.Update() #iisreset |
The actual meaning for the above code can be identified from the above mentioned blog.
For our reference, I downloaded the article and the same has been attached with this post.


Leave a comment