In the previous article, we saw how to create a basic provider hosted application. In that, the Authorization and Authentication is being done by the SharePoint Farm itself. The Web Application which we created to deploy our App was a windows authenticated web application.
In this article, let us concentrate on the Authentication process. Microsoft has come up with a new utility server (ADFS) to provide the Claims through which our SharePoint application will be able to Authenticate and proceed with Authorization.
Let us have a brief introduction about ADFS Server.
ADFS Stands for Active Directory Federation Service. The current version of ADFS is 2.0. This utility can be downloaded from the Microsoft Site and can be installed on a separate Windows 2012 Server. Active Directory Federation Services is a software component developed by Microsoft that can be installed on Windows Server operating systems to provide users with Single Sign-On access to systems and applications located across organizational boundaries. It uses a claims-based access control authorization model to maintain application security and implement federated identity.
Claims based authentication is the process of authenticating a user based on a set of claims about its identity contained in a trusted token. Such a token is often issued and signed by an entity that is able to authenticate the user by other means, and that is trusted by the entity doing the claims based authentication.
It will take a separate article to describe about the ADFS and Configuring ADFS with our SharePoint Farm. I am planning to write a separate Article regarding this soon. As of now, with this brief introduction about the ADFS, let us try to convert our previous Sample Sathish.App into a Claims Aware Provider Hosted Application.
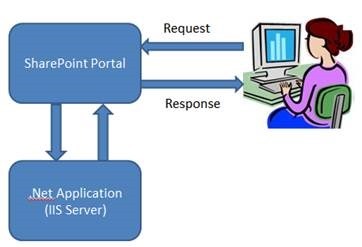
In the previous article, we saw that the SharePoint, in turn calls the IIS Server to load the .Net Applications. For our reference, refer the diagram below.
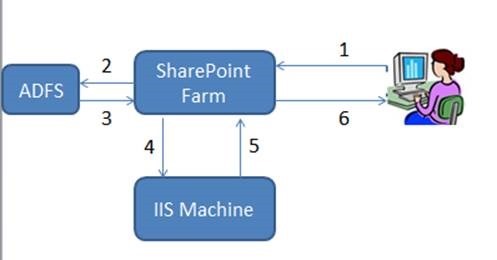
Now, by introducing the ADFS Server, the architecture would be
The request was first sent from the User to the SharePoint Farm and the user gets authenticated from the ADFS Server. Once the authentication succeeds, then we .Net application from the IIS Server will be loaded. This is very useful in the Single Sign On Scenario.
Converting into Claims Aware is nothing but a set of changes needs to be done on the web.config file. To do that, we have a tool called Identity and Access Management Tool.
The basic web.config file will look like
<?xml version="1.0"?>
<!--
For more information on how to configure your ASP.NET application, please visit
http://go.microsoft.com/fwlink/?LinkId=169433
-->
<configuration>
<!--
For a description of web.config changes for .NET 4.5 see http://go.microsoft.com/fwlink/?LinkId=235367.
The following attributes can be set on the <httpRuntime> tag.
<system.Web>
<httpRuntime targetFramework="4.5" />
</system.Web>
-->
<system.web>
<compilation debug="true" targetFramework="4.5"/>
<authorization>
<deny users="?"/>
</authorization>
<pages controlRenderingCompatibilityVersion="4.0"/>
</system.web>
<appSettings>
<add key="ClientId" value="*************************"/>
<add key="ClientSecret" value="***************************"/>
<add key="ClientSigningCertificatePath" value="C:MYCERTIFICATE.pfx"/>
<add key="ClientSigningCertificatePassword" value="********"/>
<add key="IssuerId" value="*************************"/>
</appSettings>
<system.serviceModel>
<bindings>
<basicHttpBinding>
<!--Used by app for SharePoint-->
<binding name="secureBinding">
<security mode="Transport"/>
</binding>
</basicHttpBinding>
</bindings>
<protocolMapping>
<add binding="basicHttpBinding" scheme="https" bindingConfiguration="secureBinding"/>
</protocolMapping>
</system.serviceModel>
</configuration>Now, the steps to convert this web.config file are,
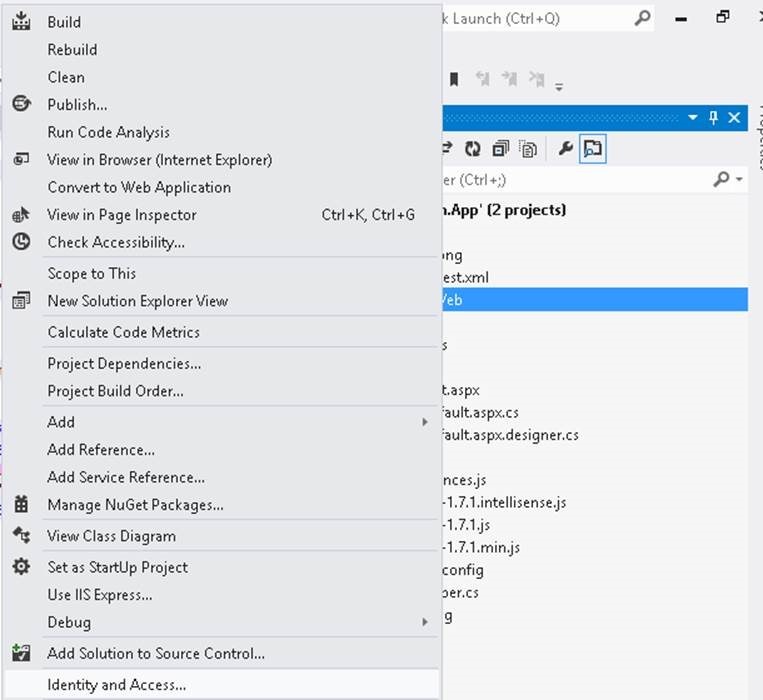
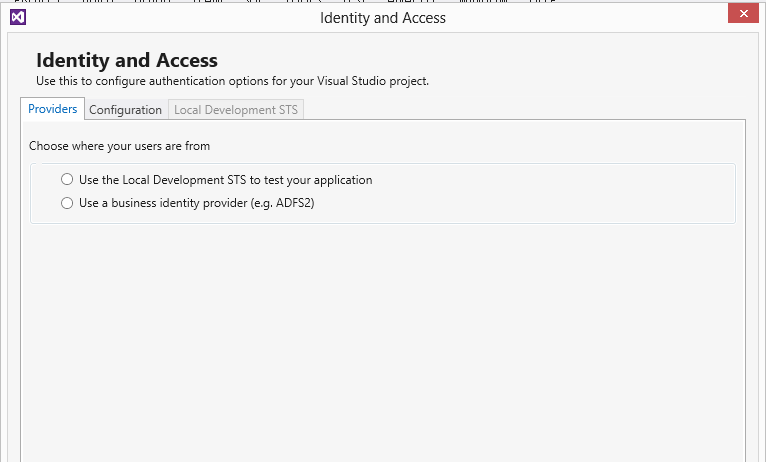
1. Go to Visual Studio and right click on the AppWeb Project.
2. Click on the Identity and Access Menu. You can see the following screen.
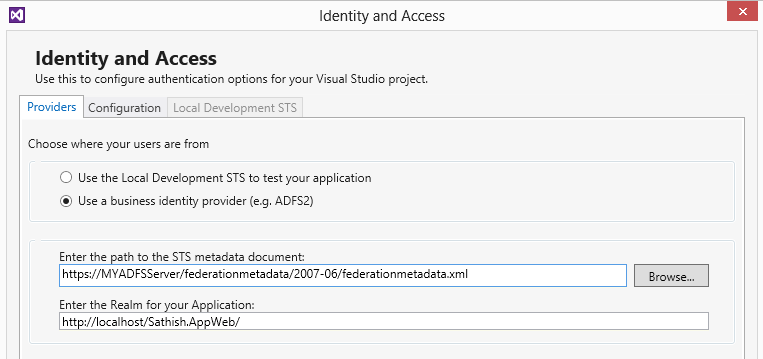
3. Select the ADFS2 Option and provide the necessary information.
4. Click OK.
5. The web.config file will be modified accordingly. The modified web.config file is as below.
<?xml version="1.0"?>
<!--
For more information on how to configure your ASP.NET application, please visit
http://go.microsoft.com/fwlink/?LinkId=169433
-->
<configuration>
<configSections>
<section name="system.identityModel" type="System.IdentityModel.Configuration.SystemIdentityModelSection, System.IdentityModel, Version=4.0.0.0, Culture=neutral, PublicKeyToken=B77A5C561934E089" />
<section name="system.identityModel.services" type="System.IdentityModel.Services.Configuration.SystemIdentityModelServicesSection, System.IdentityModel.Services, Version=4.0.0.0, Culture=neutral, PublicKeyToken=B77A5C561934E089" />
</configSections>
<!--
For a description of web.config changes for .NET 4.5 see http://go.microsoft.com/fwlink/?LinkId=235367.
The following attributes can be set on the <httpRuntime> tag.
<system.Web>
<httpRuntime targetFramework="4.5" />
</system.Web>
-->
<location path="FederationMetadata">
<system.web>
<authorization>
<allow users="*" />
</authorization>
</system.web>
</location>
<system.web>
<authentication mode="None" />
<compilation debug="true" targetFramework="4.5" />
<authorization>
<deny users="?" />
</authorization>
<pages controlRenderingCompatibilityVersion="4.0" />
<httpRuntime requestValidationMode="4.5" />
</system.web>
<appSettings>
<add key="ClientId" value="*****************"/>
<add key="ClientSecret" value="***************"/>
<add key="ClientSigningCertificatePath" value="C:MYCERTIFICATE.pfx"/>
<add key="ClientSigningCertificatePassword" value="******"/>
<add key="IssuerId" value="********************"/>
<add key="ida:FederationMetadataLocation" value="https://MYADFSSERVER/federationmetadata/2007-06/federationmetadata.xml" />
<add key="ida:Issuer" value="https://MYADFSSERVER/adfs/ls/" />
<add key="ida:ProviderSelection" value="productionSTS" />
<add key="TrustedProviderName" value="*******" />
<add key="MembershipProviderName" value="*********" />
</appSettings>
<!--<system.serviceModel>
<bindings>
<basicHttpBinding>
--><!--Used by app for SharePoint--><!--
<binding name="secureBinding">
<security mode="Transport"/>
</binding>
</basicHttpBinding>
</bindings>
<protocolMapping>
<add binding="basicHttpBinding" scheme="https" bindingConfiguration="secureBinding"/>
</protocolMapping>
</system.serviceModel>-->
<system.webServer>
<modules>
<remove name="FormsAuthentication" />
<add name="WSFederationAuthenticationModule" type="System.IdentityModel.Services.WSFederationAuthenticationModule, System.IdentityModel.Services, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089" preCondition="managedHandler" />
<add name="SessionAuthenticationModule" type="System.IdentityModel.Services.SessionAuthenticationModule, System.IdentityModel.Services, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089" preCondition="managedHandler" />
</modules>
</system.webServer>
<system.identityModel>
<identityConfiguration>
<audienceUris>
<add value="https://MYApplicationServer/Sathish.AppWeb/" />
</audienceUris>
<issuerNameRegistry type="System.IdentityModel.Tokens.ConfigurationBasedIssuerNameRegistry, System.IdentityModel, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089">
<trustedIssuers>
<add thumbprint="6C2AE960AE2DD919F000BC8C2E9E5FD4A991FF64" name="http://MYADFSSERVER/adfs/services/trust" />
</trustedIssuers>
</issuerNameRegistry>
</identityConfiguration>
</system.identityModel>
<system.identityModel.services>
<federationConfiguration>
<cookieHandler requireSsl="false" />
<!--<cookieHandler requireSsl="true" path="/" />-->
<wsFederation passiveRedirectEnabled="true" issuer="https://MYADFSSERVER/adfs/ls/" realm="https://MYAppServer/Sathish.AppWeb/" requireHttps="false" />
</federationConfiguration>
</system.identityModel.services>
</configuration>6. The same changes can be done without using the Identity and Access Tool too. Basically, we need to modify the web.config to tell the compiler that this is coming from the ADFS Server.
7. I would recommend to go with updating the web.config manually instead of relying on the Identity and Access Tool as it may not allow you to save your changes at the first time.
8. Now we are ready with our claims aware provider hosted application.
9. The last step we need to do is, add our .Net Application as the relying party trust on ADFS Server. That I will be covering on the Next Article.
Thanks for your patience to read this article. Hope this article would be very useful of creating a basic and claims aware provider hosted applications. Let me trigger the next articles over the period of time. Happy coding.

Leave a comment