Authentication is always an important and crucial part of any solution. There are various way to authenticate user/application but choosing secured and easily maintainable way will make your application strong in authentication side.
Azure Managed Identity (Prev. called Managed Service Identity (MSI)) – It is a feature of Azure Active directory, to secure authentication of other azure services with no credentials (credentials or keys will be moved out of application code). The name of the identity is same as the resource name (if the resource is deleted then managed identity of that resource will also be deleted). Well below the hood, azure managed identity is nothing but a type of service principal in Azure AD.
There are two type of Managed Identity –
- System-Assigned – This enables directly on an azure resource, then it creates service principal and credentials. It is tightly linked with azure resource, so when azure resource is deleted azure AD will remove the identity and credentials.
- User-Assigned – It is a standalone Azure resource, and it has service principal just like system-assigned. One main difference is, it can be assigned to multiple azure resources and the deletion is handled separately for each resources its assigned to.
In the below example we will get secret value out of key vault in Function App using System-Assigned managed identity,
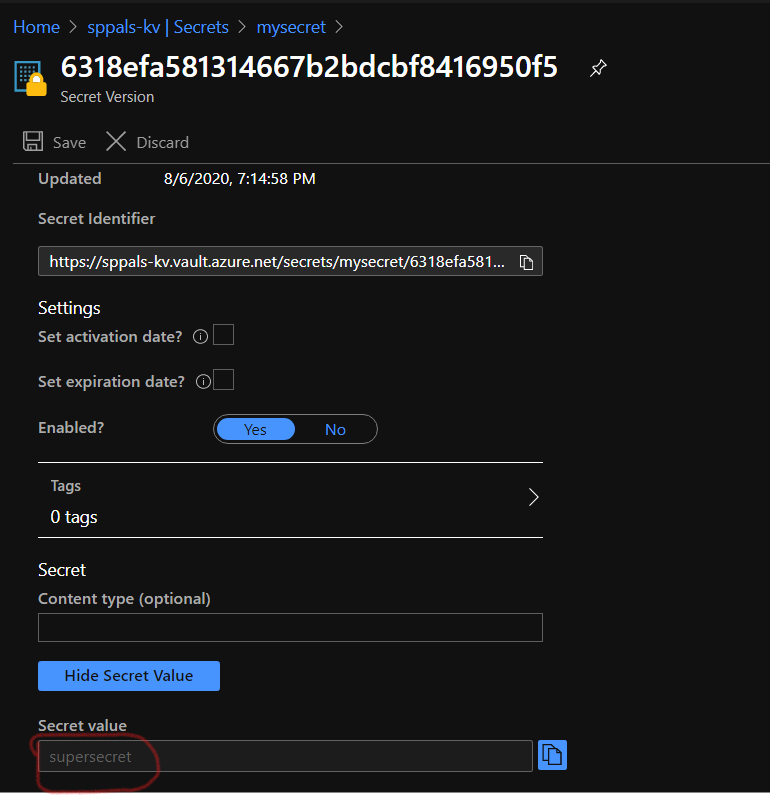
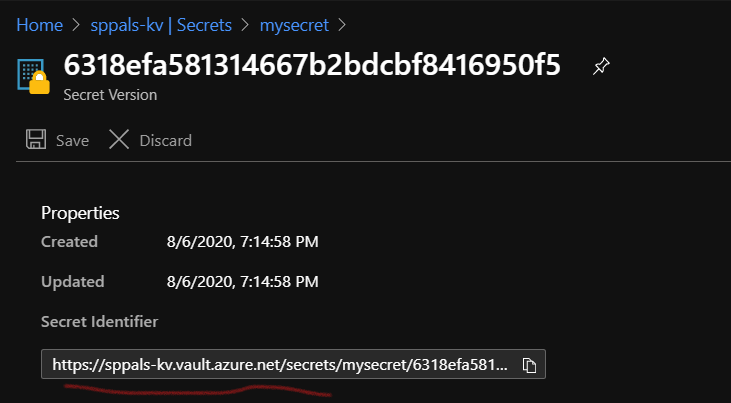
Step 1: Create a secret key in Key vault to hold secret value (we already have a key vault called – sppals-kv)
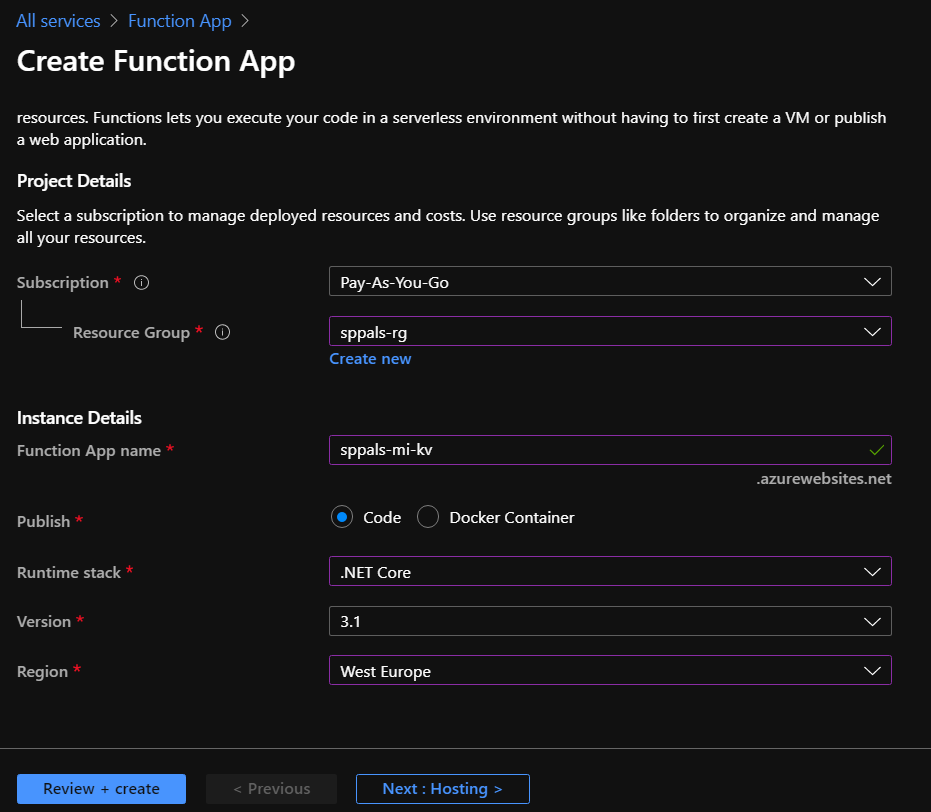
Step 2: Create a simple function app
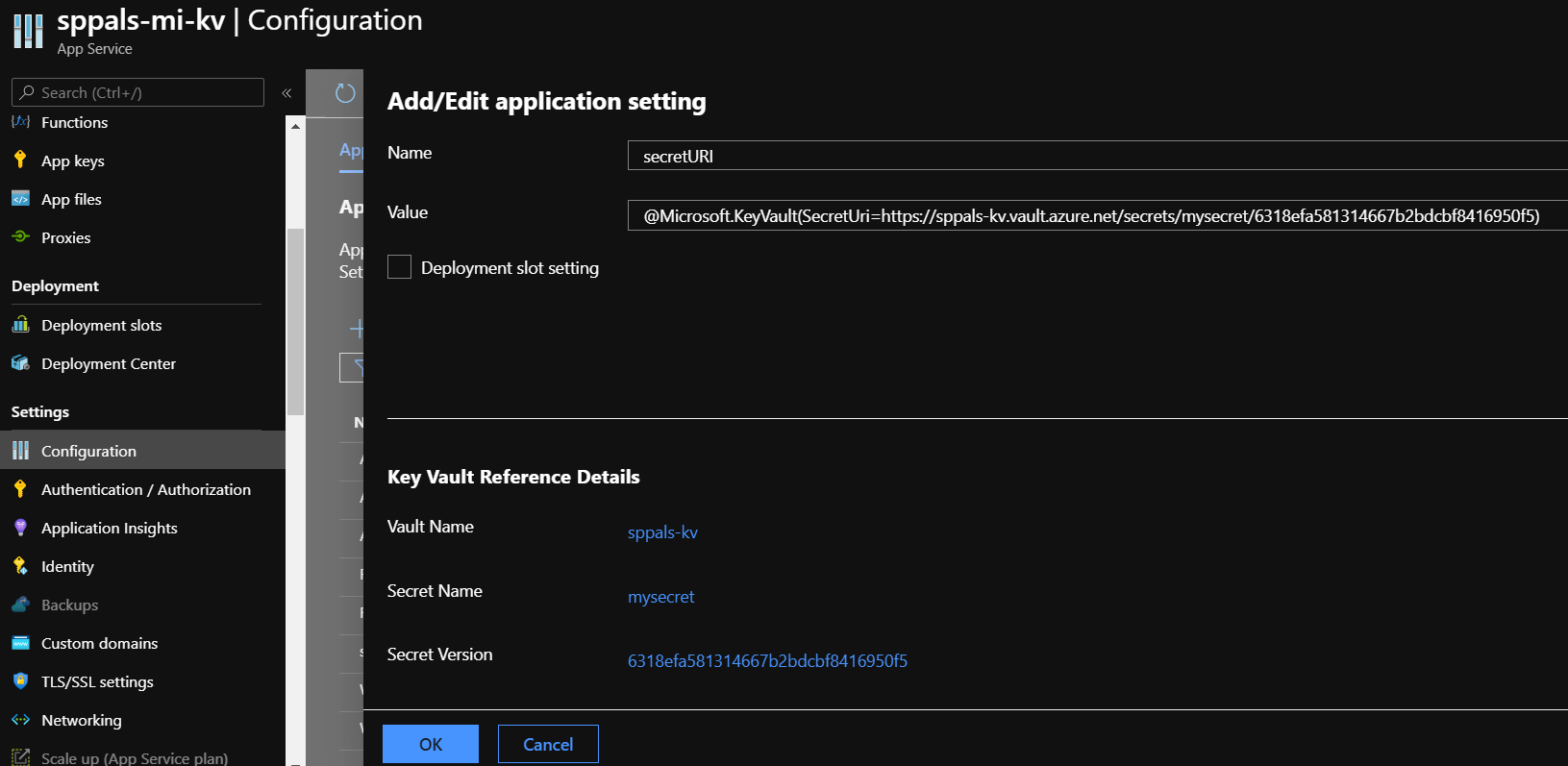
Step 2.1: Create a simple http trigger function and accessing the secret value from key vault by using uri in application config.
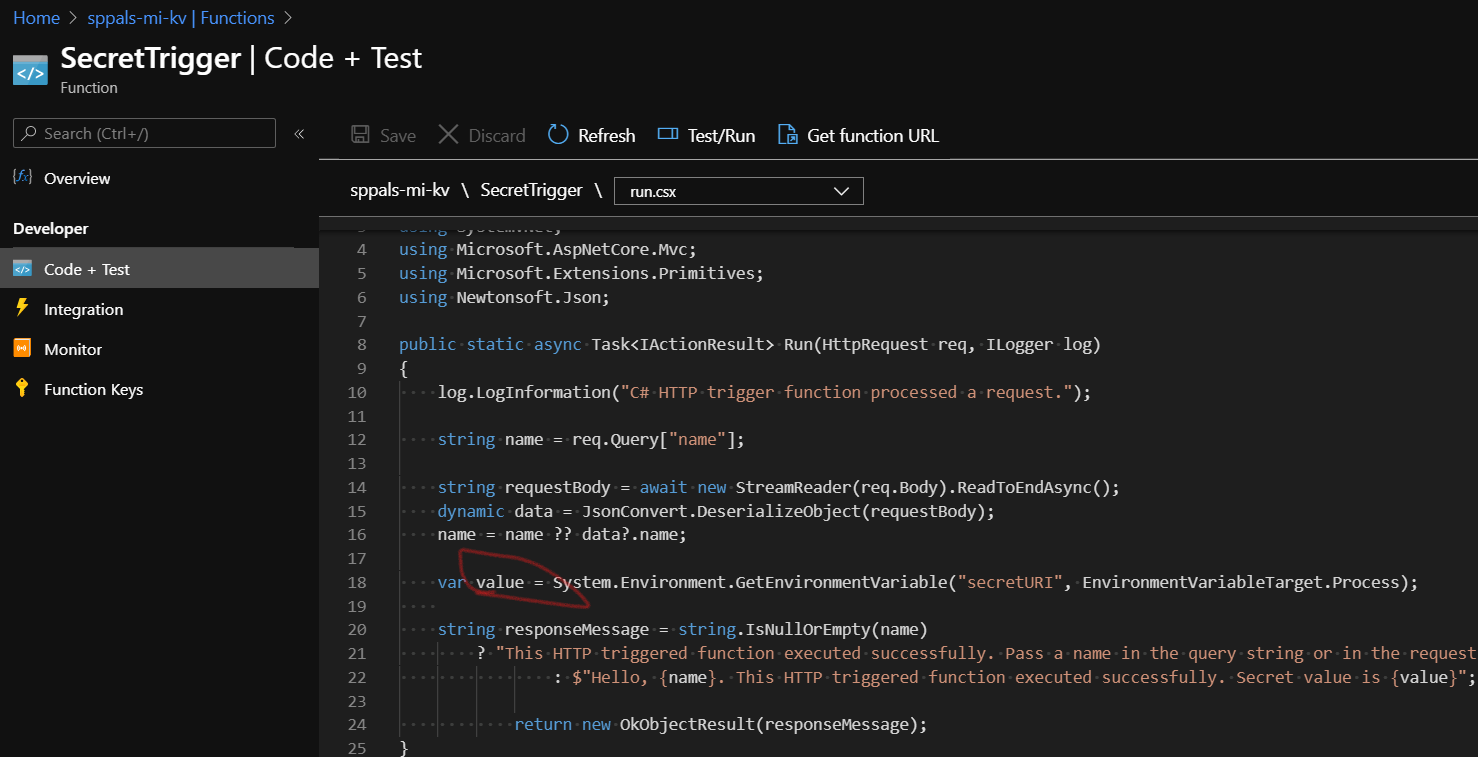
Step 2.2: To get secret key value, we need the secret identifier and keep the value in function app (we added in App config, so that we get it as env variable),
Key: secretURI
Value: @Microsoft.KeyVault(SecretUri=<secret identifier>)
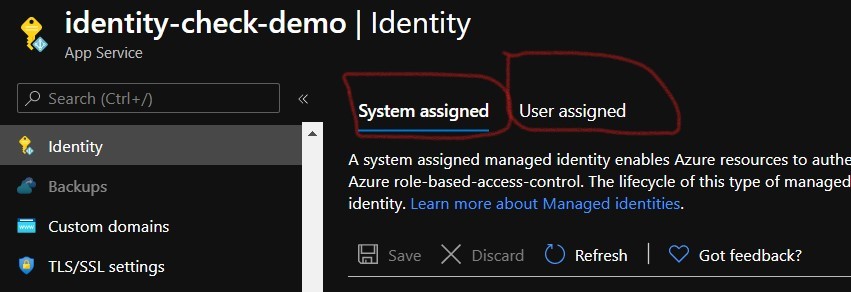
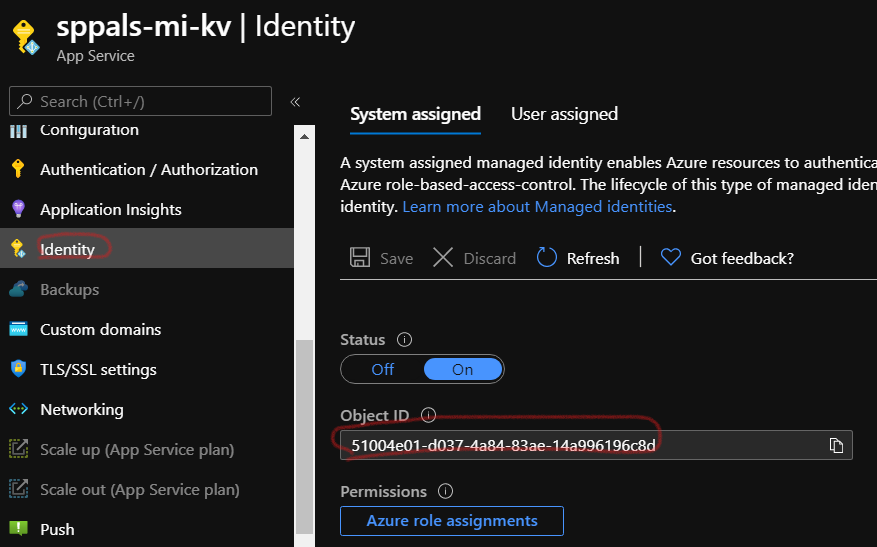
Step 2.3: Enable System Identity in function app and copy the object id
Step 3: Now we need to give System Identity (step 2.3) access to key vault from Access policy in key vault. We give only get access to secrets since we need to get value only from secrets, you can even give access to keys, certificates if required.
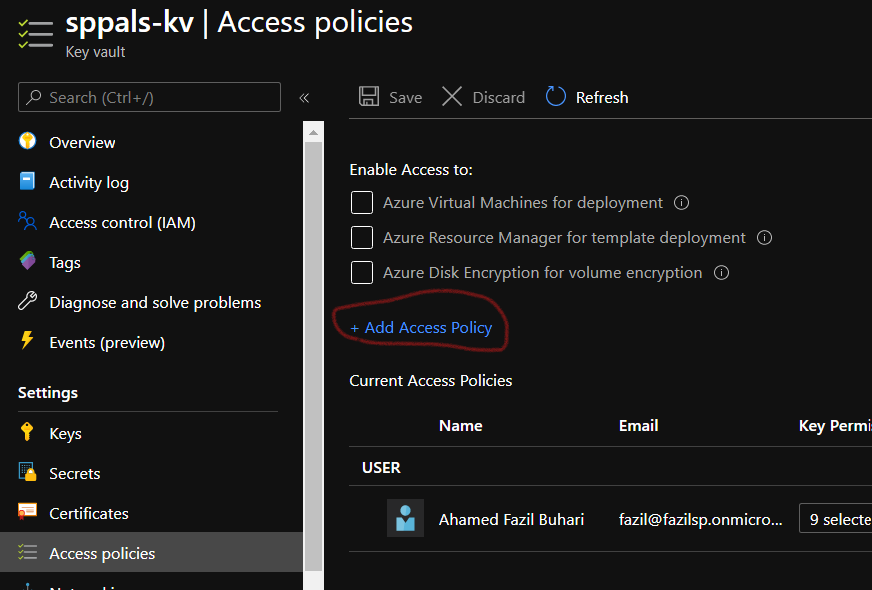
Step 3.1: Select principal by searching on object id that we got from step 2.3
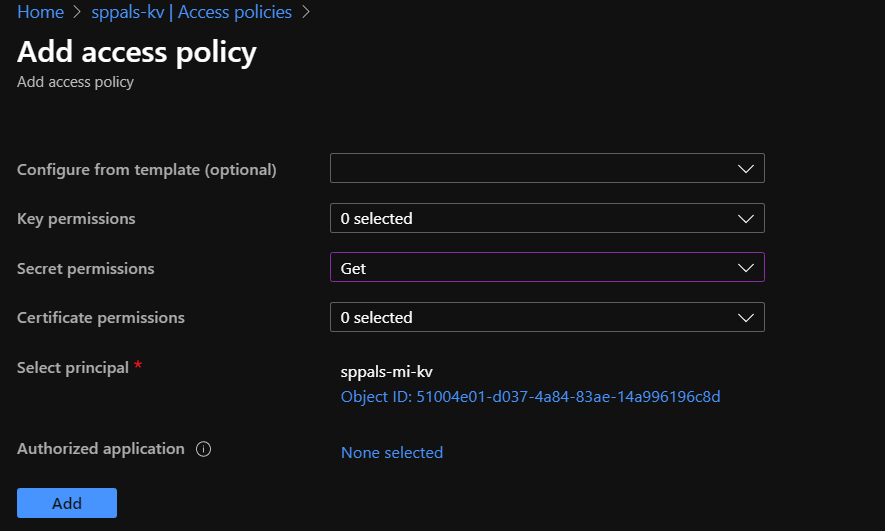
Don’t forget to hit save once we add the access policy,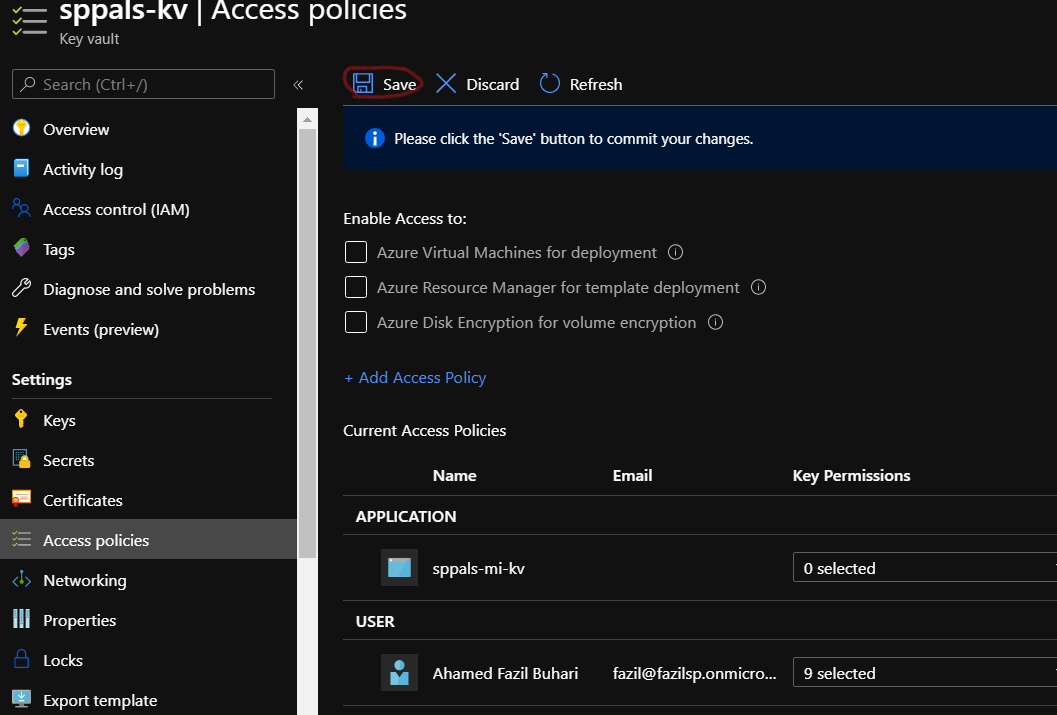
That is it. Now we successfully configured both Function App and Key Vault that talk each other through managed identity. And we can see the secret value in key vault (step 1) when we hit function app url.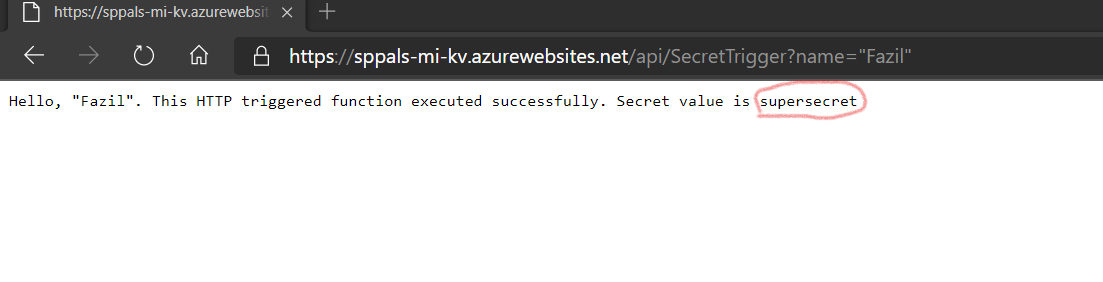
I hope this is useful for someone who wants to access azure key vault secret value in Function app using Managed Identity – configuration through azure portal.
Happy Coding
Fazil

Leave a comment